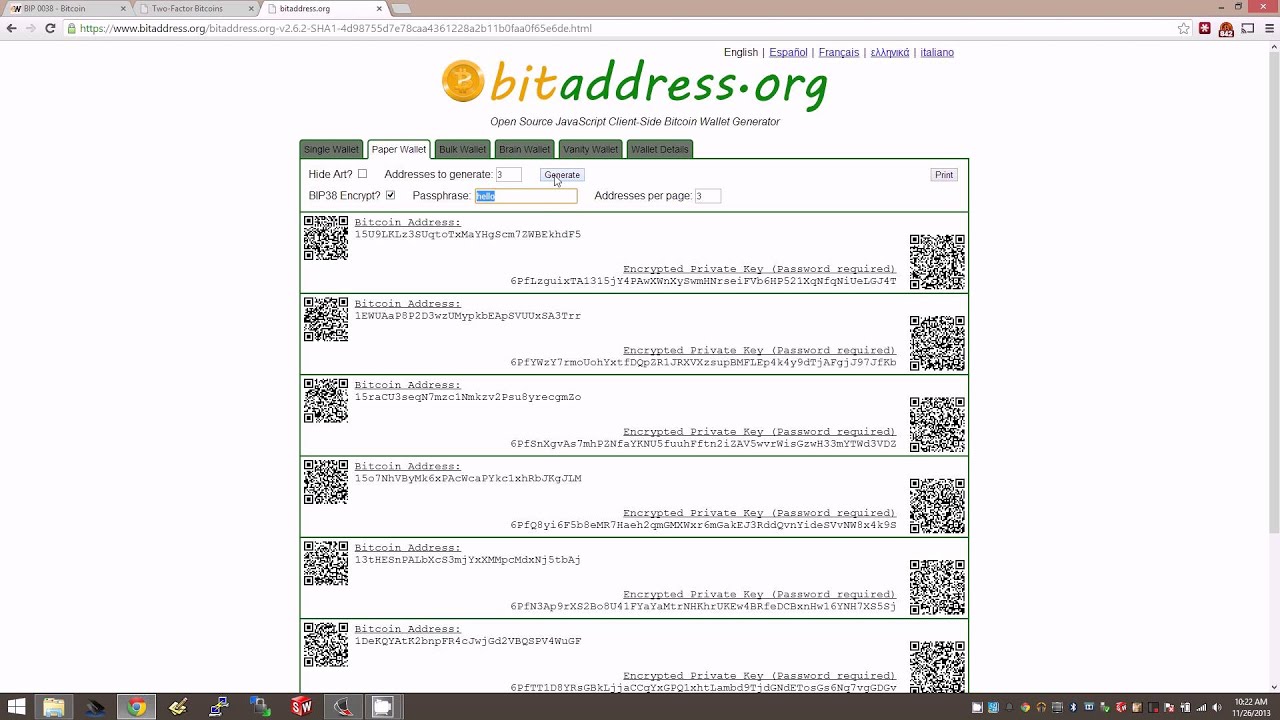
The private keys are mathematically related to all Bitcoin addresses generated for the wallet. Because the private key is the "ticket" that allows someone to spend bitcoins, it is important that these are kept secret and safe. Private keys can be kept on computer files, but are also often written on paper.
Private keys themselves are almost never handled by the user, instead the user will typically be given a seed phrase that encodes the same information as private keys.
- how to calculate btc cut off marks;
- withdraw to bitcoin core wallet?
- Private Key!
- Private and Public Keys.
- bitcoin free games.
- sites you can shop with bitcoin.
Some wallets allow private keys to be imported without generating any transactions while other wallets or services require that the private key be swept. When a private key is swept, a transaction is broadcast that sends the balance controlled by the private key to a new address in the wallet. Just as with any other transaction, there is risk of swept transactions to be double-spending.
In contrast, bitcoind provides a facility to import a private key without creating a sweep transaction. This is considered very dangerous, and not intended to be used even by power users or experts except in very specific cases. Importing keys could lead to the Bitcoins being stolen at any time, from a wallet which has imported an untrusted or otherwise insecure private key - this can include private keys generated offline and never seen by someone else [1] [2]. In Bitcoin, a private key is a bit number, which can be represented one of several ways.
Here is a private key in hexadecimal - bits in hexadecimal is 32 bytes, or 64 characters in the range or A-F. Wallet software may use a BIP 32 seed to generate many private keys and corresponding public keys from a single secret value. This is called a hierarchical deterministic wallet , or HD wallet for short.
- Bitcoin Private Keys: Everything You Need To Know!
- bitcoin 9th december?
- how does bitcoin increase value.
- Private key - Bitcoin Wiki.
- github bitcoin-qt.
- is buying bitcoin legal in germany.
The seed value, or master extended key , consists of a bit private key and a bit chain code , for bits in total. The seed value should not be confused with the private keys used directly to sign Bitcoin transactions. Users are strongly advised to use HD wallets, for safety reasons: An HD wallet only needs to be backed up once typically using a seed phrase ; thereafter in the future, that single backup can always deterministically regenerate the same private keys.
Therefore, it can safely recover all addresses, and all funds sent to those addresses. Non-HD wallets generate a new randomly-selected private key for each new address; therefore, if the wallet file is lost or damaged, the user will irretrievably lose all funds received to addresses generated after the most recent backup. When importing or sweeping ECDSA private keys, a shorter format known as wallet import format is often used, which offers a few advantages.
Wallet import format is the most common way to represent private keys in Bitcoin.
Subscribe to stay updated
For private keys associated with uncompressed public keys, they are 51 characters and always start with the number 5 on mainnet 9 on testnet. Private keys associated with compressed public keys are 52 characters and start with a capital L or K on mainnet c on testnet.
An issuer of physical bitcoins must be trustworthy and trusted. Even if trustworthy, users are rightful to be skeptical about a third party with theoretical access to take their funds. A physical bitcoin that cannot be compromised by its issuer is always more intrinsically valuable than one that can. A two-factor physical bitcoin solution is highly useful to individuals and organizations wishing to securely own bitcoins without any risk of electronic theft and without the responsibility of climbing the technological learning curve necessary to produce such an environment themselves.
Two-factor physical bitcoins allow a secure storage solution to be put in a box and sold on the open market, greatly enlarging the number of people who are able to securely store bitcoins. Existing methodologies for creating two-factor physical bitcoins are limited and cumbersome. At the time of this proposal, a user could create their own private key, submit the public key to the physical bitcoin issuer, and then receive a physical bitcoin that must be kept together with some sort of record of the user-generated private key, and finally, must be redeemed through a tool.
The fact that the physical bitcoin must be kept together with a user-produced private key negates much of the benefit of the physical bitcoin - the user may as well just print and maintain a private key. A standardized password-protected private key format makes acquiring and redeeming two-factor physical bitcoins simpler for the user.
Instead of maintaining a private key that cannot be memorized, the user may choose a passphrase of their choice.

The passphrase may be much shorter than the length of a typical private key, short enough that they could use a label or engraver to permanently commit their passphrase to their physical Bitcoin piece once they have received it. By adopting a standard way to encrypt a private key, we maximize the possibility that they'll be able to redeem their funds in the venue of their choice, rather than relying on an executable redemption tool they may not wish to download.
Password and passphrase-protected private keys enable new practical use cases for sending bitcoins from person to person. Someone wanting to send bitcoins through postal mail could send a password-protected paper wallet and give the recipient the passphrase over the phone or e-mail, making the transfer safe from interception of either channel. A user of paper wallets or Bitcoin banknote-style vouchers "cash" could carry funded encrypted private keys while leaving a copy at home as an element of protection against accidental loss or theft.
A user of paper wallets who leaves bitcoins in a bank vault or safety deposit box could keep the password at home or share it with trusted associates as protection against someone at the bank gaining access to the paper wallets and spending from them. The foreseeable and unforeseeable use cases for password-protected private keys are numerous.
It is proposed that the resulting Base58Check-encoded string start with a '6'. The number '6' is intended to represent, from the perspective of the user, "a private key that needs something else to be usable" - an umbrella definition that could be understood in the future to include keys participating in multisig transactions, and was chosen with deference to the existing prefix '5' most commonly observed in Wallet Import Format which denotes an unencrypted private key.
It is proposed that the second character ought to give a hint as to what is needed as a second factor, and for an encrypted key requiring a passphrase, the uppercase letter P is proposed. To keep the size of the encrypted key down, no initialization vectors IVs are used in the AES encryption. Rather, suitable values for IV-like use are derived using scrypt from the passphrase and from using a bit hash of the resulting Bitcoin address as salt. Encrypting a private key without the EC multiplication offers the advantage that any known private key can be encrypted.
The party performing the encryption must know the passphrase. Encrypting a private key with EC multiplication offers the ability for someone to generate encrypted keys knowing only an EC point derived from the original passphrase and some salt generated by the passphrase's owner, and without knowing the passphrase itself. Only the person who knows the original passphrase can decrypt the private key. A code known as an intermediate code conveys the information needed to generate such a key without knowledge of the passphrase.
Bitcoin Private Key: An Easy-To-Understand Overview
This methodology does not offer the ability to encrypt a known private key - this means that the process of creating encrypted keys is also the process of generating new addresses. On the other hand, this serves a security benefit for someone possessing an address generated this way: if the address can be recreated by decrypting its private key with a passphrase, and it's a strong passphrase one can be certain only he knows himself, then he can safely conclude that nobody could know the private key to that address.
The person who knows the passphrase and who is the intended beneficiary of the private keys is called the owner. He will generate one or more "intermediate codes", which are the first factor of a two-factor redemption system, and will give them to someone else we'll call printer , who generates a key pair with an intermediate code can know the address and encrypted private key, but cannot decrypt the private key without the original passphrase.
An intermediate code should, but is not required to, embed a printable "lot" and "sequence" number for the benefit of the user. The proposal forces these lot and sequence numbers to be included in any valid private keys generated from them.
Subscribe to RSS
An owner who has requested multiple private keys to be generated for him will be advised by applications to ensure that each private key has a unique lot and sequence number consistent with the intermediate codes he generated. The "lot" and "sequence" number are combined into a single 32 bit number.
For programs that generate batches of intermediate codes for an owner , it is recommended that lot numbers be chosen at random within the range and that sequence numbers are assigned starting with 1. Steps performed by owner to generate a single intermediate code, if lot and sequence numbers are being included:.
The party generating the Bitcoin address has the option to return a confirmation code back to owner which allows owner to independently verify that he has been given a Bitcoin address that actually depends on his passphrase, and to confirm the lot and sequence numbers if applicable.
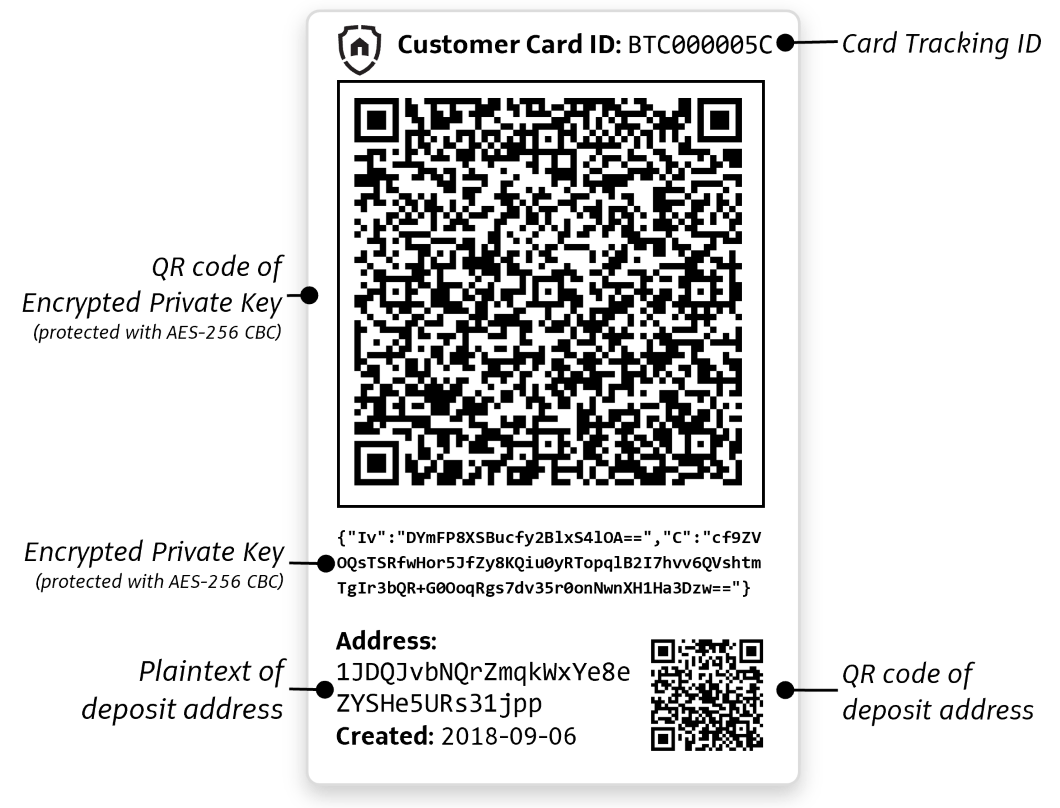 Bitcoin encrypted private key
Bitcoin encrypted private key
 Bitcoin encrypted private key
Bitcoin encrypted private key
 Bitcoin encrypted private key
Bitcoin encrypted private key
 Bitcoin encrypted private key
Bitcoin encrypted private key
 Bitcoin encrypted private key
Bitcoin encrypted private key
 Bitcoin encrypted private key
Bitcoin encrypted private key
 Bitcoin encrypted private key
Bitcoin encrypted private key
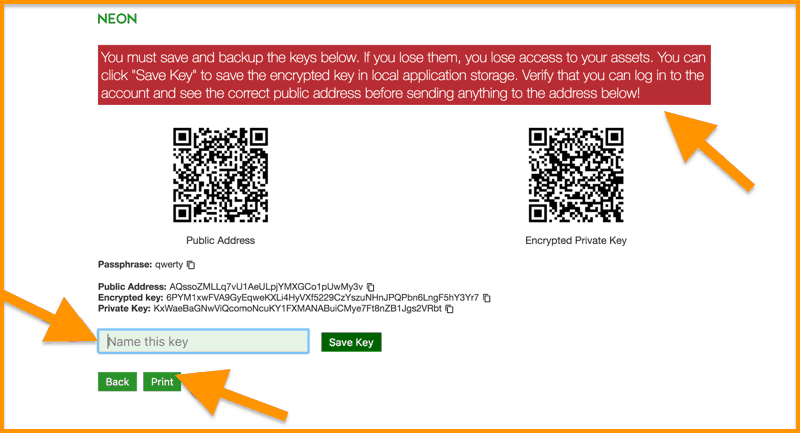 Bitcoin encrypted private key
Bitcoin encrypted private key
Related bitcoin encrypted private key
Copyright 2020 - All Right Reserved