
In fact, knowing that this will be the case, there is little reason for Alice to try this in the first place.
What is bitcoin? - CNNMoney
She will then attempt to fork the chain before the transaction with Charlie, adding a block which includes a transaction in which she pays herself:. And unless Alice is able to solve the proof-of-work at least as fast as everyone else in the network combined — roughly, that means controlling more than fifty percent of the computing power — then she will just keep falling further and further behind.
Of course, she might get lucky. We can, for example, imagine a scenario in which Alice controls one percent of the computing power, but happens to get lucky and finds six extra blocks in a row, before the rest of the network has found any extra blocks. In this case, she might be able to get ahead, and get control of the block chain. But this particular event will occur with probability. Of course, this is not a rigorous security analysis showing that Alice cannot double spend. The security community is still analysing Bitcoin, and trying to understand possible vulnerabilities.
How the Bitcoin protocol actually works
The proof-of-work and mining ideas give rise to many questions. How much reward is enough to persuade people to mine? How does the change in supply of infocoins affect the Infocoin economy? Will Infocoin mining end up concentrated in the hands of a few, or many? These are all great questions, but beyond the scope of this post.
I may come back to the questions in the context of Bitcoin in a future post.
- bitcoin vs ftse!
- wanneer moet je bitcoins kopen?
- Get the Latest from CoinDesk.
- How does Bitcoin work? - Bitcoin.
To use Bitcoin in practice, you first install a wallet program on your computer. You can see the Bitcoin balance on the left — 0. What you do is tell your wallet program to generate a Bitcoin address. You then send your Bitcoin address to the person who wants to buy from you. You could do this in email, or even put the address up publicly on a webpage.
This is safe, since the address is merely a hash of your public key, which can safely be known by the world anyway. The person who is going to pay you then generates a transaction. Line 1 contains the hash of the remainder of the transaction, 7c This is used as an identifier for the transaction. Lines 3 and 4 tell us that the transaction has one input and one output, respectively. Line 6 tells us the size in bytes of the transaction. That comes later. Lines 7 through 11 define the input to the transaction. In particular, lines 8 through 10 tell us that the input is to be taken from the output from an earlier transaction, with the given hash , which is expressed in hexadecimal as ae Line 11 contains the signature of the person sending the money, Again, these are both in hexadecimal.
This seems like an inconvenient restriction — like trying to buy bread with a 20 dollar note, and not being able to break the note down.
Looking Beyond The Hype - Into The Blockchain
The solution, of course, is to have a mechanism for providing change. Lines 12 through 14 define the output from the transaction. In particular, line 13 tells us the value of the output, 0. Line 14 is somewhat complicated. The main thing to note is that the string a7db6f You can now see, by the way, how Bitcoin addresses the question I swept under the rug in the last section: where do Bitcoin serial numbers come from?
In fact, the role of the serial number is played by transaction hashes. In the transaction above, for example, the recipient is receiving 0.
And so on. There are two clever things about using transaction hashes instead of serial numbers. Second, by operating in this way we remove the need for any central authority issuing serial numbers. Instead, the serial numbers can be self-generated, merely by hashing the transaction. Ultimately, this process must terminate. This can happen in one of two ways. This is a special transaction, having no inputs, but a 50 Bitcoin output.
In other words, this transaction establishes an initial money supply. You can see the deserialized raw data here , and read about the Genesis block here. With the exception of the Genesis block, every block of transactions in the block chain starts with a special coinbase transaction.
This is the transaction rewarding the miner who validated that block of transactions. It uses a similar but not identical format to the transaction above. You can read a little more about coinbase transactions here. The obvious thing to do is for the payer to sign the whole transaction apart from the transaction hash, which, of course, must be generated later. Currently, this is not what is done — some pieces of the transaction are omitted. This makes some pieces of the transaction malleable , i. I gather that this malleability is under discussion in the Bitcoin developer community, and there are efforts afoot to reduce or eliminate this malleability.
In the last section I described how a transaction with a single input and a single output works. Line 1 contains the hash of the remainder of the transaction. As in the single-input-single-output case this is set to 0, which means the transaction is finalized immediately.
Bitcoin, Explained for Beginners
Lines 7 through 19 define a list of the inputs to the transaction. Each corresponds to an output from a previous Bitcoin transaction. Line 11 contains the signature, followed by a space, and then the public key of the person sending the bitcoins. Lines 12 through 15 define the second input, with a similar format to lines 8 through And lines 16 through 19 define the third input.
The first output is defined in lines 21 and Line 21 tells us the value of the output, 0. The main thing to take away here is that the string e8c One apparent oddity in this description is that although each output has a Bitcoin value associated to it, the inputs do not. Of course, the values of the respective inputs can be found by consulting the corresponding outputs in earlier transactions. In a standard Bitcoin transaction, the sum of all the inputs in the transaction must be at least as much as the sum of all the outputs. The only exception to this principle is the Genesis block, and in coinbase transactions, both of which add to the overall Bitcoin supply.
If the inputs sum up to more than the outputs, then the excess is used as a transaction fee. This is paid to whichever miner successfully validates the block which the current transaction is a part of. One nice application of multiple-input-multiple-output transactions is the idea of change. Suppose, for example, that I want to send you 0.
I can do so by spending money from a previous transaction in which I received 0. The solution is to send you 0. Those 0. Of course, it differs a little from the change you might receive in a store, since change in this case is what you pay yourself. But the broad idea is similar. That completes a basic description of the main ideas behind Bitcoin.
But I have described the main ideas behind the most common use cases for Bitcoin. How anonymous is Bitcoin? Many people claim that Bitcoin can be used anonymously. This claim has led to the formation of marketplaces such as Silk Road and various successors , which specialize in illegal goods. However, the claim that Bitcoin is anonymous is a myth.
 Technical bitcoin explanation
Technical bitcoin explanation
 Technical bitcoin explanation
Technical bitcoin explanation
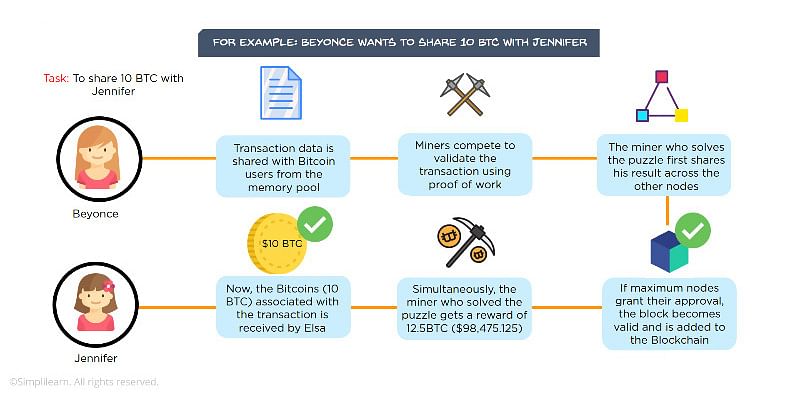 Technical bitcoin explanation
Technical bitcoin explanation
 Technical bitcoin explanation
Technical bitcoin explanation
 Technical bitcoin explanation
Technical bitcoin explanation
 Technical bitcoin explanation
Technical bitcoin explanation
Related technical bitcoin explanation
Copyright 2020 - All Right Reserved