
Bitcoin's blockchain, for example, uses a public ledger and the lack of transparency in Bitcoin's transactions can put individuals at risk if the ledger shows they have a large holding of coins, which can be an invitation to hacker thieves. It is also a tricky situation for merchants who accept cryptocurrency payments. If their public address remains fixed and known, everyone would know about their customers' possible identities and their subsequent transactions. Bitcoin and Ethereum are two of the most popular blockchain networks but they both use a public distributed ledger.
Public blockchain networks have led to many participants questioning the security features surrounding the anonymity of the networks. Concerns have increased about hacking financial data and stealing cryptocurrency coins by tracking a person's identity through their transaction history, such as when they cash their digital coins.
As a result, the need for privacy-enhancing technology embedded into blockchain networks has grown. Stealth addresses were proposed by Peter Todd in The stealth address' mechanism uses a combination of various public and private keys that are dynamic and for one-time use only. Some stealth addresses are created using the elliptic-curve Diffie-Hellman protocol. However, there have been various protocols and types of stealth addresses created over the years, which have included features that protect an individual's privacy and the development of private cryptocurrencies.
- spek laptop untuk mining bitcoin?
- how exactly is bitcoin mined?
- tether bitcoin manipulation.
The race is on for developers to create enhanced privacy features that completely hide a user's identity and the amount of money or crypto assets within their digital wallets. Stealth addresses protect the privacy of receivers of cryptocurrencies by requiring the sender to use a random, one-time address for every transaction. As a result, numerous transactions done with the same recipient are not able to be linked since each transaction has a one-time address.
For example, Monero is a cryptocurrency that was developed specifically to ensure the privacy of its participants. According to a report issued in by the U. Attorney General's Cyber Digital Task Force, cybercrime has an added layer of complexity when criminals use the blockchain ecosystem. Also, some crypto-asset exchanges operate outside the United States and its regulatory requirements.
The report went on to say that fighting financial crime has faced increased challenges, in part, due to decentralized platforms such as non-public or private blockchains including those with "anonymity-enhanced cryptocurrencies. The crimes that involve blockchain networks and cryptocurrencies are not necessarily new and may include the following:. Stealth addresses and private blockchains make it more challenging for officials to trace transactions involving illegal behavior. The U. Department of Justice mentions specific cryptocurrencies by name that offer "anonymity enhanced cryptocurrencies AECs or privacy coins," which include Monero and Zcash.
Struggling to create your first Bitcoin wallet? Here's how to get started.
On August 13, , the Department of Justice announced the dismantling of cyber campaigns used to finance terrorist activity involving the al-Qassam Brigades. Stealth addresses offer enormous opportunities for protecting privacy involving financial transactions and data. As cybercrime increases, businesses and individuals will likely look for ways in which to protect themselves from having their data and financial account information exposed to fraudsters.
However, considering the ability of stealth addresses to hide illegal activity, it's safe to say that there will be increased scrutiny in the coming years by regulatory agencies, tax authorities, and governments. For example, both privacy coins and stealth addresses have been a method of tax avoidance leading the Internal Revenue Service IRS to take action.
Operation Hidden Treasure is designed to crack down on tax evasion by cryptocurrency participants.
Subscribe to RSS
For example, a user let's call him Ken on a stealth address-supported blockchain is holding five cryptocurrency tokens. Ken has complete control over the tokens as long as he holds them. If he wishes to send all of them to Paul, he will generate a transaction output, which will announce to the network that Ken is sending five tokens to Paul. As a result, Paul becomes the rightful owner of the five tokens.
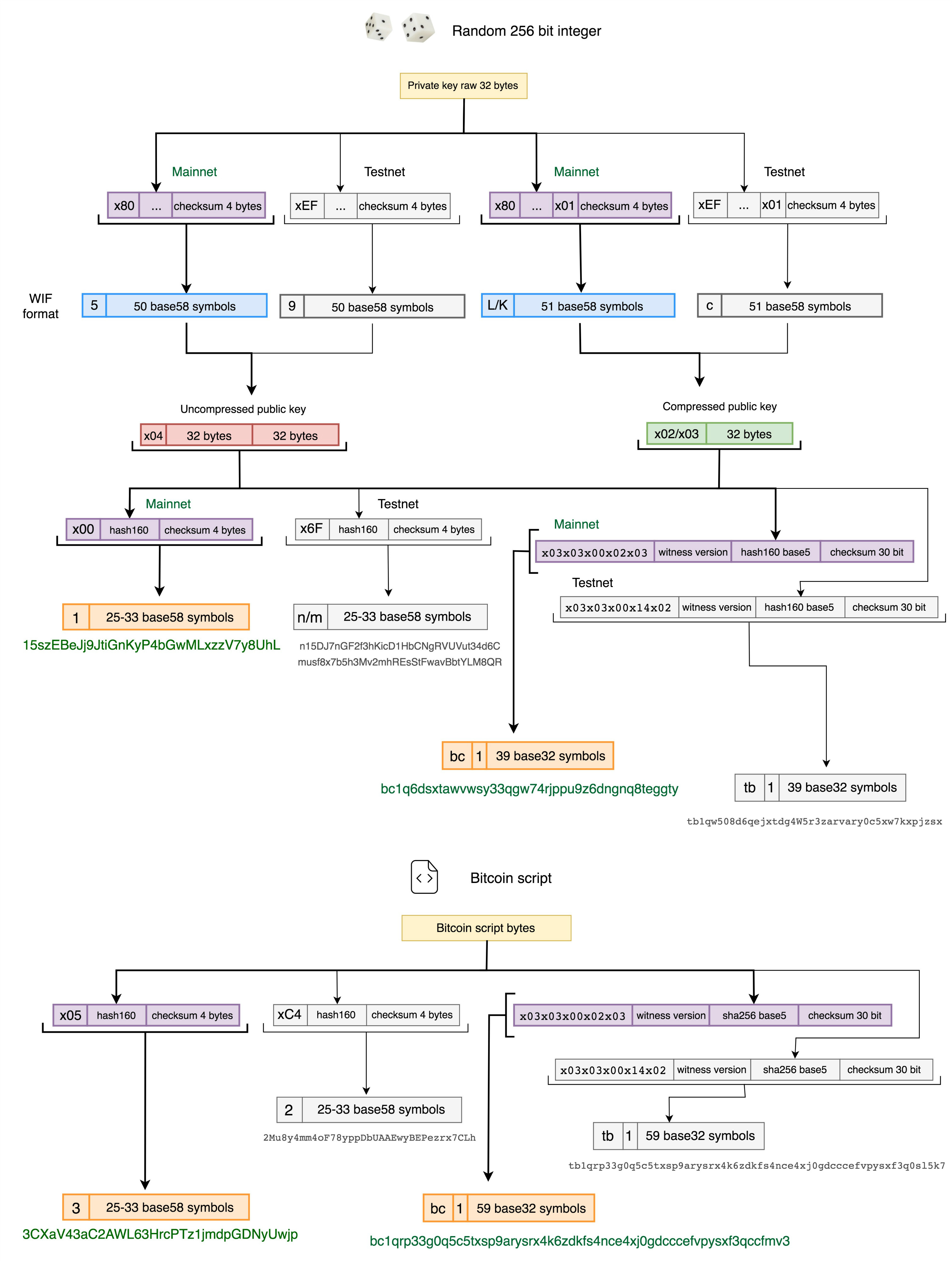
Chapter 4. Keys, Addresses, Wallets
Ken's wallet will use both Paul's public view key and his public spend key and club it with random strings of data that generate the one-time unique public key for Paul's output. While others on the network can see a transaction getting recorded, no one other than Ken and Paul will be aware that it took place between Ken and Paul. Using his own wallet's private view key, Paul will be able to locate the transaction on the blockchain and retrieve it in his wallet.
Using the one-time private key that corresponds to the one-time public key for the transaction, Paul will gain the right to spend the cryptocurrency.
Why does my BitPay wallet's bitcoin address keep changing? – BitPay Support
Nowhere in this process are sender's or receiver's wallet addresses made public. As these randomly generated, one-time use addresses are created for each transaction on behalf of the recipient, stealth addresses add an additional layer of privacy. Monero, which is known for its privacy and anonymity, is using stealth addresses as the basis for its transaction. Peter Todd. Department of Justice. Accessed Mar. Your Privacy Rights. To change or withdraw your consent choices for Investopedia.
At any time, you can update your settings through the "EU Privacy" link at the bottom of any page.
These choices will be signaled globally to our partners and will not affect browsing data. We and our partners process data to: Actively scan device characteristics for identification. I Accept Show Purposes. Your Money. Personal Finance. Your Practice. Overview of all products. Overview of HubSpot's free tools. Marketing automation software. Free and premium plans.
Sales CRM software.

Customer service software. Content management system software. Premium plans. Connect your favorite apps to HubSpot. See all integrations. We're committed to your privacy.
HubSpot uses the information you provide to us to contact you about our relevant content, products, and services. You may unsubscribe from these communications at any time. For more information, check out our privacy policy. If you want to buy or sell items with Bitcoin , you need to be able to send and receive your funds from a certain location, kind of like sending and receiving mail through a mailbox. A Bitcoin address indicates the source or destination of a Bitcoin payment.
Most blockchain experts recommend generating a new Bitcoin address each time you send or receive a payment, though. This personal security measure makes it harder for people to trace where your Bitcoin funds come from and where they go. To get a Bitcoin address, you first need to download a Bitcoin wallet, which is software that allows you to securely send, receive, and store Bitcoin funds in the Bitcoin network.
Bitcoin wallets also store your private key, which is essentially your Bitcoin password. The software will generate a brand new Bitcoin address for you every time you create an invoice or receive a payment request for Bitcoins too. There are four types of Bitcoin wallets that you can use: mobile, web, desktop, and hardware. To combat this security issue, consider only letting fingerprint authentication open your mobile wallet app.
If someone knows a few of your personal details, like your phone number, email address, and birthday, they can impersonate you, telling your wireless service provider that you need to switch your number to a new phone -- their phone. Then, they can go to your email account, click "forgot my password", and your email service provider will text a "change my password" code straight to their phone.
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
 Destination bitcoin address
Destination bitcoin address
Related destination bitcoin address
Copyright 2020 - All Right Reserved