
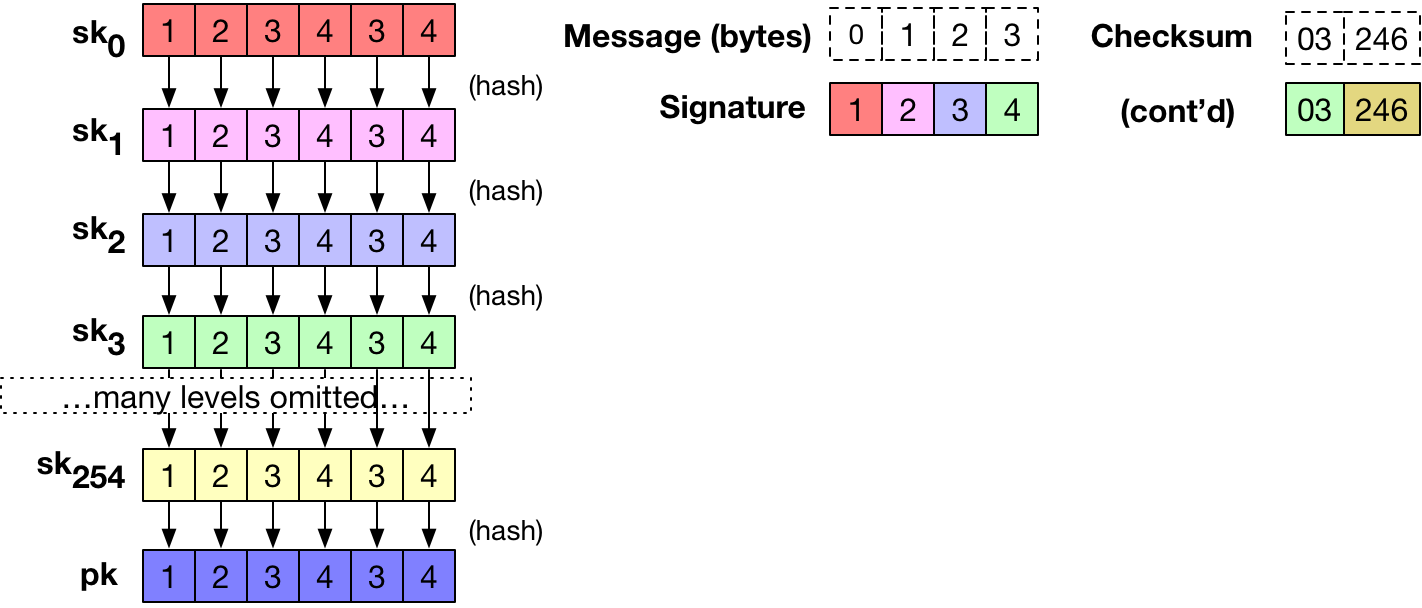
This gives her random numbers. These random numbers are her signature and she publishes them along with the message. Note that now Alice's private key is used and should never be used again. The other random numbers that she did not use for the signature she must never publish or use. Preferably she should delete them.
Bitcoin Is Not Quantum-Safe, And How We Can Fix It When Needed
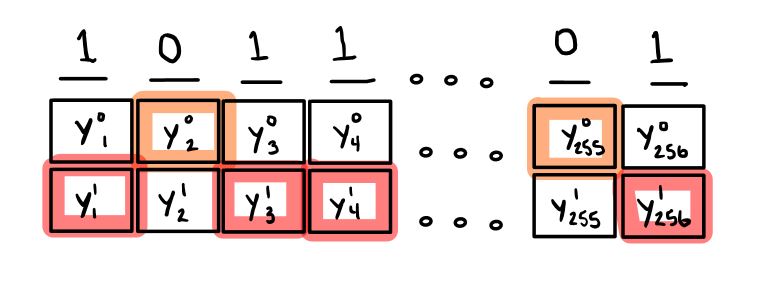
Otherwise others will later be able to create false signatures. Then Bob wants to verify Alice's signature of the message. He also hashes the message to get a bit hash sum. Then he uses the bits in the hash sum to pick out of the hashes in Alice's public key. He picks the hashes in the same manner that Alice picked the random numbers for the signature. That is, if the first bit of the message hash is a 0, he picks the first hash in the first pair, and so on. Then Bob hashes each of the random numbers in Alice's signature. This gives him hashes.
If these hashes exactly match the hashes he just picked from Alice's public key then the signature is ok. If not, then something is wrong. Thus no one else can create the proper list of random numbers for the signature.

And after Alice has published the signature others still do not know the other random numbers and thus can not create signatures that fits other message hashes. The security of Lamport signatures is based on security of the one way hash function, the length of its output and the quality of the input. For a hash function that generates an n-bit message digest, the ideal preimage and 2nd preimage resistance on a single hash function invocation implies on the order of 2 n operations and 2 n bits of memory effort to find a collision under a classical computing model.
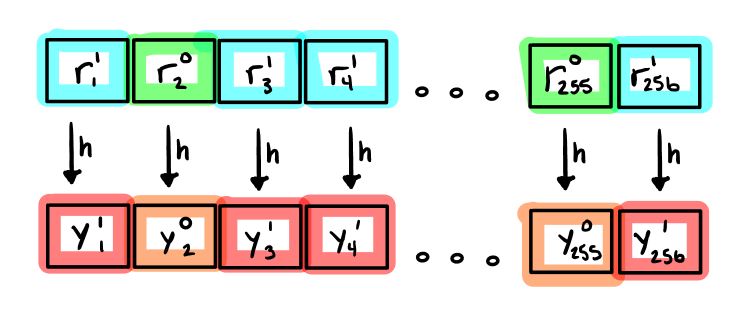
In Lamport signatures, each bit of the public key and signature is based on short messages requiring only a single invocation to a hash function.
Navigation menu
For each private key y i,j and its corresponding z i,j public key pair, the private key length must be selected so performing a preimage attack on the length of the input is not faster than performing a preimage attack on the length of the output. For example, in a degenerate case, if each private key y i,j element was only 16 bits in length, it is trivial to exhaustively search all 2 16 possible private key combinations in 2 15 operations to find a match with the output, irrespective of the message digest length.
Therefore a balanced system design ensures both lengths are approximately equal.
Based on Grover's algorithm, a quantum secure system, the length of the public key elements z i,j , the private key elements y i,j and the signature elements s i,j must be no less than 2 times larger than the security rating of the system. That is:. However caution should be taken as the idealistic work estimates above assume an ideal perfect hash function and are limited to attacks that target only a single preimage at a time.
A masterplan is everything you need to make it big in trading. The market gives you exactly what you want. You win if you choose to win and lose if you chose to lose. Make a wise choice! Don't sit on your ass and wait for things to happen.
Lamport signature
Get out there and take the risk. It's only through risk that we discover our best potential. Trading is not a complicated game where the guy with an IQ of takes all the money. Teeka Tiwari Predicts that Bitcoin will go through the roof as the covidtriggered recession continues to kick in. Moreover, In bitcoin each transaction is charged a network fee based upon transaction size in terms of bytes, not in terms of amount. I know this question is really old, but you should look into IOTA iota.
Sign up to join this community.
The best answers are voted up and rise to the top. Stack Overflow for Teams — Collaborate and share knowledge with a private group. Create a free Team What is Teams? Learn more.
How Do Cryptographic/Digital Signatures in Bitcoin Work? | CaptainAltcoin
Why don't crypto-currencies use the Lamport signature scheme? Ask Question. Asked 4 years, 2 months ago. Active 3 years, 5 months ago. Viewed 2k times. Improve this question. MaiaVictor MaiaVictor 1, 4 4 silver badges 11 11 bronze badges. I don't have a reference, however.
 Lamport signatures bitcoin
Lamport signatures bitcoin
 Lamport signatures bitcoin
Lamport signatures bitcoin
 Lamport signatures bitcoin
Lamport signatures bitcoin
 Lamport signatures bitcoin
Lamport signatures bitcoin
 Lamport signatures bitcoin
Lamport signatures bitcoin
Related lamport signatures bitcoin
Copyright 2020 - All Right Reserved