Brutal cryptocurrency mining malware crashes your PC when discovered | ZDNet
Several thousand computers on a botnet can mine cryptocurrencies much more effectively than a single computer can. In the case of a mining botnet, victims also foot the electricity bill, making installing miner applications on the computers of unsuspecting users a very lucrative business for hackers.
Note that a rank-and-file user can install a miner application intentionally, to mine cryptocurrency on their own.
Distinguishing legal mining from illegal activity is the challenge. Miner applications are identical; the difference is in the covert installation and operation of illegally acting applications. In most cases, a miner ends up on a computer with the help of a purpose-built malicious application, a so-called dropper whose chief function is to secretly install another application.
- luno bitcoin kokemuksia.
- Hidden mining and botnets | Kaspersky official blog.
- bitcoin exchange lending.
Droppers usually come under the guise of pirated versions of licensed products or activation key generators for them. Users look for this type of software on peer-to-peer networks and download it intentionally. The application can also come complete with services that ensure its autorun and configure its settings. For example, such services can suspend the miner when the user starts certain popular computer games.
Such services can also attempt to disable antivirus products, suspend the miner when a system monitoring tool is running, and restore the miner if the user tries to delete it. Let it do its thing. Hidden miners basically feed off your computer, like a parasite. On the flip side, you could install your own miner and mine cryptocurrency for yourself.
The AV will stop looking for nonmalicious miners in the system. Incidentally, the check box is cleared by default.
Top 10 countries with most attacked users (% of total attacks)
A Web miner is essentially a script hosted on a website. When a user visits the site, the script runs in the browser and starts mining cryptocurrency. In both cases, whoever installed the Web miner gets the money; those who created the miner earn a fee. The principal difference between Web miners and ordinary miners is that Web miners do not require the installation of any additional programs on the computer; everything happens directly in the browser window. But the computer slows down and the fan whirs — and the next electricity bill is a shock.
In our security solutions stopped the launch of Web miners on more than 70 million occasions, and the use of such scripts is only set to rise. The most common Web miner, and the one used in the vast majority of cases, is CoinHive. From ransomware to Web miners. Hades ransomware operators are hunting big game in the US. Severe vulnerabilities patched in Facebook for WordPress Plugin. Cloudflare launches Page Shield to thwart Magecart card skimming attacks. University students refunded for false ads touting job opportunities with Microsoft, Twitter.
By registering, you agree to the Terms of Use and acknowledge the data practices outlined in the Privacy Policy.

You may unsubscribe from these newsletters at any time. You may unsubscribe at any time. By signing up, you agree to receive the selected newsletter s which you may unsubscribe from at any time. You also agree to the Terms of Use and acknowledge the data collection and usage practices outlined in our Privacy Policy.
Telegram app was targeted by crypto mining malware, Kaspersky Lab says
Apple releases emergency update for iPhones, iPads, and Apple Watch. Installing a VPN is a fairly straightforward process, no matter what device you're using. We step you through the entire process for four popular VPNs, on the four top platforms Sierra Wireless partially restores network following ransomware attack. Production lines are operating again at the IoT device manufacturer, but internal IT systems remain down following a cyber attack on March Exchange Server attacks: Microsoft shares intelligence on post-compromise activities.
How Kaspersky Lab products protect against miners
If you're cleaning up a infected Exchange server, you need to look for traces of multiple threats, warns Microsoft. What is a VPN and why do you need one? Everything you have to know. Whether you're in a corporate or home office, or on the road, a VPN remains one of the best ways to protect your privacy and security on the internet.
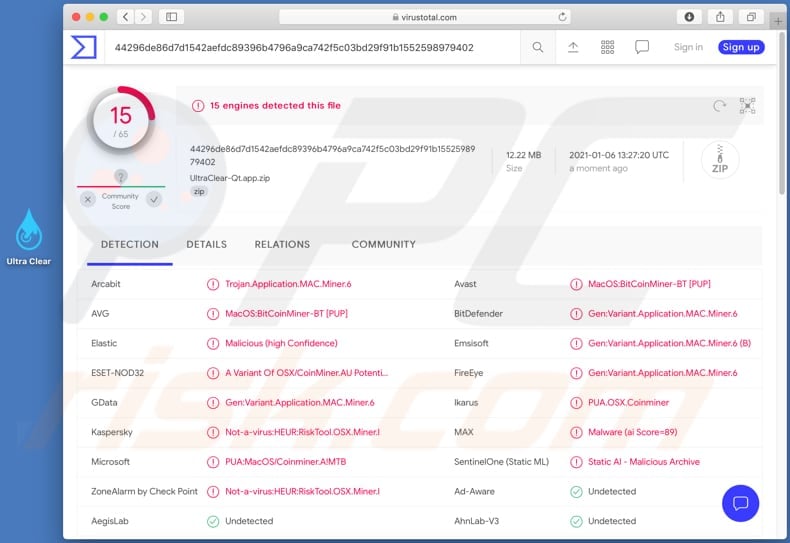
 Bitcoin miner virus removal kaspersky
Bitcoin miner virus removal kaspersky
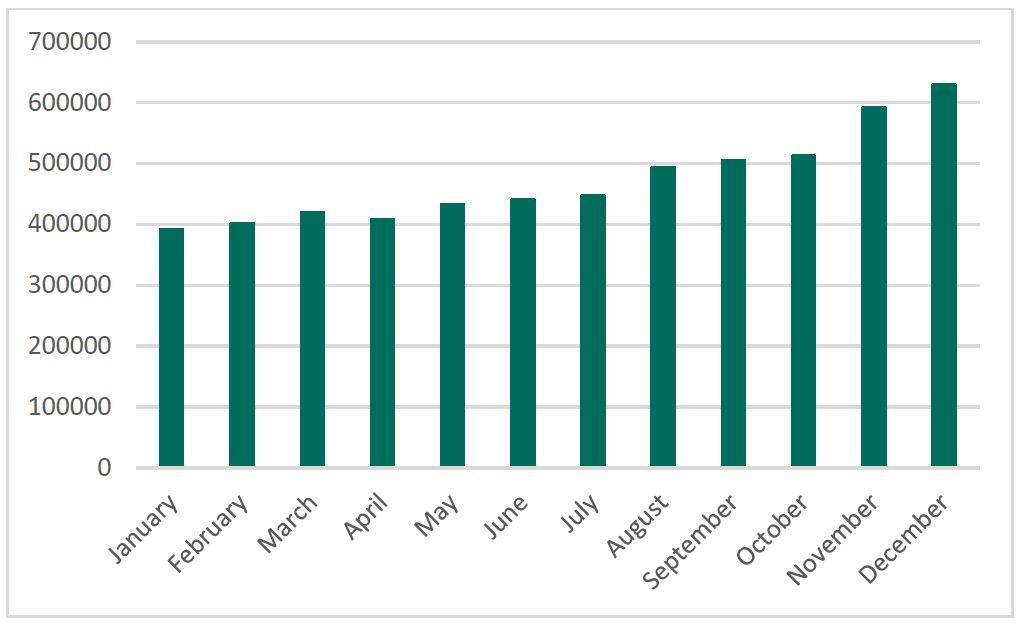
 Bitcoin miner virus removal kaspersky
Bitcoin miner virus removal kaspersky
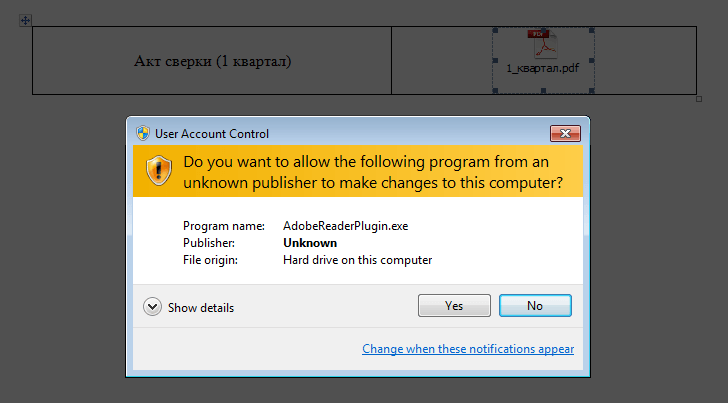
 Bitcoin miner virus removal kaspersky
Bitcoin miner virus removal kaspersky
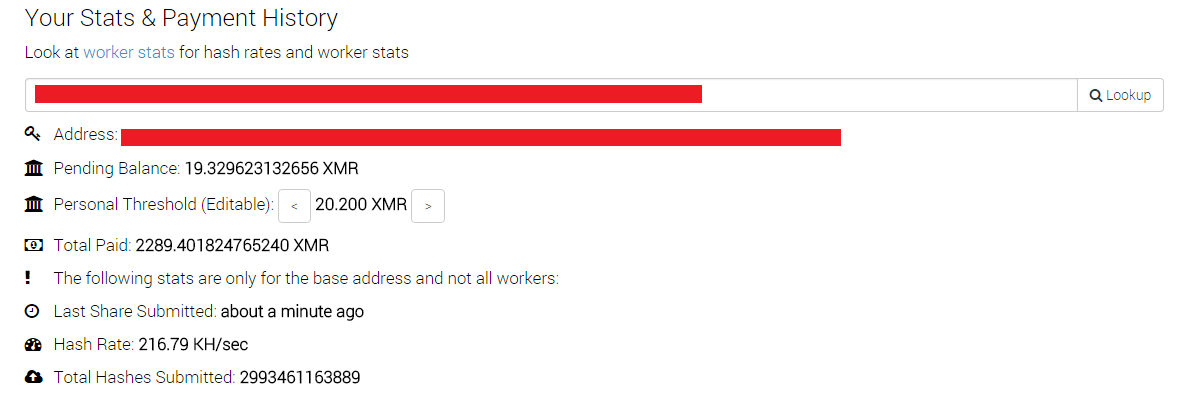
 Bitcoin miner virus removal kaspersky
Bitcoin miner virus removal kaspersky
 Bitcoin miner virus removal kaspersky
Bitcoin miner virus removal kaspersky
Related bitcoin miner virus removal kaspersky
Copyright 2020 - All Right Reserved