Users in Australia complain after Google blocks local websites, after Australia seeks to force tech firms to pay for news content. What is making people upset down under is that users were not informed of the change, or advised how to find news articles when searching, with some reporting they initially believed it was an issue only affecting them.
The Guardian reported that people impact by the experiment can get around the block by searching in a private browser window, such as in incognito mode in Google Chrome. This is because Australia is pressing ahead with a new law to force big name tech firms to pay local publishers for any news content they utilise on their respective platforms. The legislation is currently being reviewed by an Australian Senate committee, and a vote is expected early this year.
Australian crypto exchange plans legal action against NAB for account closures |
The move is being strongly opposed by Google and Facebook , despite Australia touting the new law as a way to protect independent journalism. Google in November additionally signed copyright agreements with six French newspapers and magazines, including Le Monde and Le Figaro. According to the Malaysian Central Bank no funds were stolen during the incident and the bank's payment systems remained unaffected and operational. In March , two Venezuelan men were arrested for jackpotting, where they installed malicious software or hardware on ATMs to force the machines to dispense huge volumes of cash on demand.
The pair were sentenced to federal prison in November for conspiracy to commit bank robbery. Two financial firms were among the various U. The actors are accused by the United States of stealing 31 terabytes of academic and commercial information in a campaign dating as far back as Nine Iranians have been charged by the United States, which claims the group acts on behalf of the Islamic Revolutionary Guard Corps and has imposed sanctions on numerous individuals and companies in the country as a result.
In February , it was revealed that thirty-six people from seven countries had been indicted in the United States for their alleged involvement in the Infraud Organization, which law enforcement officials say sells stolen personal and financial information. More than half a billion dollars was lost by the victims, the U. Department of Justice said, with a trail going back to October The organization was said to have more than 10, registered members who bought and sold illicit products including malware, data from credit card dumps, and information needed for identity fraud. Initial reports raised concerns of a Russian connection to the attack, as it came a week after a media report that Dutch intelligence agents had infiltrated the Russian threat group APT On December 19, , YouBit, a South Korean cryptocurrency exchange, was hacked for the second time that year and had 17 percent of it's digital currency stolen by attackers, which forced it to stop trading.
It later declared bankruptcy as a result. The attack used sophisticated Business Email Compromise. The attackers used an unusual ransomware variant named Hermes, but this was likely a distraction for their main objective of using administrative credentials to move funds to Cambodia, the United States, and Sri Lanka. The attack is suspected of being performed by a group that has repeatedly intruded on bank networks to carry out thefts.
Most of the stolen money was recovered, and two men were arrested in Sri Lanka after they attempted to withdraw funds. The Securities and Exchange Commission announced in September that hackers might have accessed inside information from the Edgar database, which contains market-sensitive filings for companies listed on U. The commission did not realize the intrusion, which took place in through a software vulnerability in a test filing component, could have leaked company secrets until August The identity of the hackers is unknown, although reports have suggested the perpetrators are based in Eastern Europe.
In one of the biggest data breaches on record, the credit reporting agency Equifax announced in October that more than million customer records had been compromised, including some sensitive data such as birth dates and 12, U. According to the U. Once inside the network, the attackers found unencrypted usernames and passwords for other databases, spent seventy-six days on the network, eventually accessing forty-eight different datasets.
However, the company has avoided fines from the banking regulators in eight U. On February 10 , the U. The hackers also stole PII from 30, customers. In January 16, , Recorded Future, a security firm known for analyzing state-sponsored attacks, attributed the attack to the Lazarus Group in the North Korean government. In December , after a number of DDoS attacks on Russian banks throughout the previous month, the Russian Federal Security Service FSB announced that it had discovered pending cyber attacks intended to impact a range of major Russian banks.
Servers and command centers purportedly to be used in these attacks were located in the Netherlands and owned by BlazingFast, a Ukrainian hosting company. BlazingFast said it had no information about the asserted attack and that it was unable to find any malicious data. The Dutch Ministry of Security and Justice said that it was aware its infrastructure could be used for cyber attacks elsewhere, and that if the Russian authorities decided to investigate, the Dutch investigating authorities would provide assistance.
They reached a peak volume of 3.
How the Commonwealth Bank helped a Bitcoin fraud suspect accused of laundering billions
No evidence exists that such action, complementary to the DDoS attacks, was attempted. In late , the Securities and Exchange Commission SEC sued three Chinese traders, arguing that they had installed malware on the networks of two law firms to steal confidential, market-moving information on mergers and acquisitions.
- sheraton btc;
- Facebook versus Australia.
- News Ticker.
- Firstmonie;
- Bloomberg - Are you a robot?.
Hong Kong refused a request to extradite one of the men to the United States in The bank only used basic checks to assess whether cards were genuine, for example merely inspecting whether the debit card would expire in the future instead of making sure the exact expiration date matched its records. Visa and Mastercard had both previously warned of an increase in the type of fraud seen in this case, which used the magnetic strip to verify the transaction.
On November 5, , as the weekend began, the gang started making fraudulent transactions with the card details it had calculated. Almost 9, accounts were affected, or 6. Tesco Bank halted all online and contactless transactions after a day of struggling to block all the fake purchases reported in the United States, Spain, and Brazil. In mid, a number of Indian banks replaced or changed security codes on 3. Multiple security firms noted the attackers used tactics and techniques similar to the Bangladesh heist four months previously.
The attackers sent the money to accounts in Thailand, Cambodia, Australia, Hong Kong and Taiwan, and those accounts belonged to shell companies associated with Chinese-organized crime syndicates. The funds were later returned at the request of the Nigerian bank.
Paying publishers
Department of Justice indictment of Park Jin Hyok. According to the Japanese government, the attackers used forged cards with data of roughly 3, pieces of customer information stolen from Standard Bank to withdraw cash from ATMs located in Tokyo and 16 prefectures across Japan.
Anonymous claimed responsibility as part of Operation Icarus, a campaign against central banks. In April , an anonymous source leaked 2. The journalists shared the The revelations had far-reaching effects, including the resignation of the Icelandic prime minister, a number of tax evasion investigations, and the closure of Mossack Fonseca. DownSec Belgium claims to fight against corrupt government abuses.
This toolkit allowed them to delete records of transfer requests, bypass validity checks, delete records of logins, manipulate reporting of balances, and stop attached printers from printing transaction logs. Although the malware was custom-designed to steal from the Bangladesh central bank, the toolkit could potentially be used against other banks in the SWIFT system running Alliance Access software. Furthermore, they timed the thefts so that it would be the weekend in Bangladesh when the Federal Reserve reached out to confirm the transactions, and then it would be the weekend in New York when the Bangladesh central bank employees instructed the Federal Reserve to cancel the transactions.
In late , hackers threatened to disable systems at three Greek banks unless they paid a bitcoin ransom. When the banks refused, they had their sites repeatedly knocked out for several hours. The group claiming responsibility for the extortion said it was part of the Armada Collective, which had previously targeted numerous businesses including Cloudflare and Proton Mail, although some investigators believed it might have been a copycat attack using the same name. In November , a teenager was sentenced to community service after carrying out four DDoS attacks against Nordea and Swedbank.
Beginning on June 12, , the Shanghai Composite Index began to plummet, and by June 19 it had fallen by 13 percent. Chinese stock markets continued to fall throughout July and August, and again in January and February Although there is no public evidence, some have speculated that the initial sudden crash may have been caused by a cyber attack. Tien Phong did not name the bank that had been the source of the fraudulent transfer request.
Australian crypto exchange plans legal action against NAB for account closures
In February , reports indicated that records for almost 80 million customers were stolen from Anthem, a U. The stolen data was taken over the course of several weeks and included personal information, such as social security numbers. A subsequent report by the California Department of Insurance pointed to a national government as the likely culprit for the attack, and suggested the initial breach occurred in February , meaning Anthem was exposed for a year before the compromise was discovered.
Several weeks after the incident was disclosed, fellow insurer Premera Blue Cross announced that around 11 million customer accounts had been compromised by attackers, and rival CareFirst admitted 1. Some researchers believe the thefts were carried out by the same group.
In early , a bank in Ecuador was the first known victim in a series of multimillion dollar heists that used compromised payments systems to then transfer funds over the SWIFT interbank messaging network. The heist came to light in a lawsuit Banco brought against Wells Fargo, which it alleged failed to spot red flags when it approved the fraudulent transaction. The litigation was settled in February but no details were disclosed. The Metel banking Trojan, which was discovered in , was repurposed by a criminal gang in to steal directly from bank ATMs and even manipulate the Russian exchange rate.
Method: Multiple: malware, phishing and browser vulnerabilities Type: Theft. This meant they could withdraw unlimited amounts of money, automatically resetting the account balance after each transaction. Researchers at Kaspersky, who first reported on the operation, said the gang comprised fewer than ten members and had made no infections outside Russia. However, there is no evidence the attackers profited from the movement. Metel had infected , devices and more than financial institutions in , according to researchers at Group IB.
In October , reports revealed that criminals had written malware to infect Windows-based ATMs and steal millions from machines primarily in Eastern Europe. The malware, dubbed Tyupkin, was spread by a CD and once installed it laid low, only accepting commands on Sunday and Monday nights. Mules could type in a randomly generated key allowing them to withdraw 40 banknotes. Similar to the Ploutus campaign in Latin America, the Tyupkin group had an organized gang of mules to access the ATMs and collect the money. Eight Romanian and Moldovan nationals were arrested in connection with the scheme in January In October , a group claiming to be affiliated with the so-called Islamic State hacked the internal networks of the Warsaw Stock Exchange and posted dozens of login credentials for brokers online.
In August , the first reports emerged that account information and home addresses for 83 million customers were exposed after attackers stole login credentials from a JPMorgan Chase employee.
Related Stories
However, the bank said the attackers had not accessed more sensitive information, such as social security numbers. JPMorgan discovered the breach after reportedly finding the same group on a website for a charity race that it sponsors. Nine people so far have been charged in the ongoing probe. A Russian national was extradited from Georgia to the United States in September , although he denied that he was the central hacker in the attacks. The federal authorities in New York said the man worked with an international syndicate from to to steal customer information, which was used in numerous crimes including a spam email campaign to falsely tout stocks and shares to ramp up the price.
In September , he pleaded guilty to six felony charges in connection with the data breach and other cybercrimes, and he faces up to a lifetime in prison. In January , a Florida man pleaded guilty to charges linked to funds processed through Coin. The supposed ringleader was extradited to the United States in and, according to media reports, entered a plea deal with prosecutors. In July , the European Central Bank ECB announced that hackers had breached the security of a database holding email addresses and other contact data submitted by people registering for events at the bank. The ECB said most of the stolen data was encrypted, and no internal systems or sensitive market data had been compromised as the database was separate to those systems.
Approximately 20, people had their information exposed in non-encrypted form. The attack came to light after the supposed perpetrators emailed the ECB demanding a ransom payment on July The bank informed the German police, although no further information is available about the investigation. The means by which it gained access to the data is unknown. The group warned PrivatBank customers to transfer their money to state-owned banks. CyberBerkut may have connections to the Russian government, but the relative lack of sophistication of their attacks has led some experts to conclude that official links are unlikely.
With China the largest source of bitcoin trading at the time, the announcement sent the value of the currency down by around 40 percent. The perpetrators of the DDoS attack have not been publicly identified. In September , the malware Ploutus was built to be installed directly on ATMs in order to give an attacker privileged rights, including the ability to dispense cash on demand via SMS or using a keyboard attached to the machine.
 Australian banks reportedly freeze accounts of bitcoin users
Australian banks reportedly freeze accounts of bitcoin users
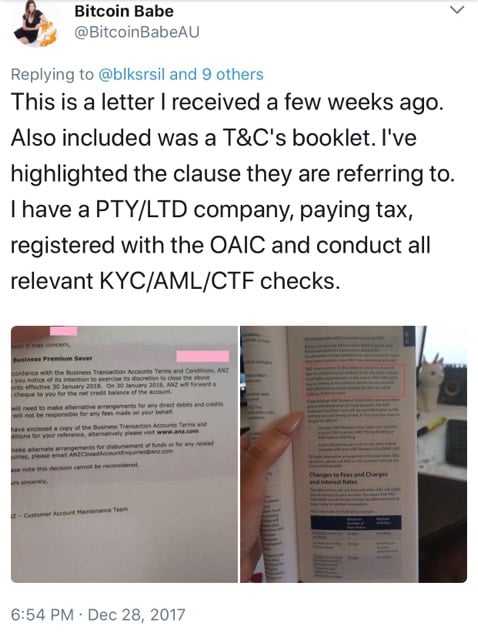 Australian banks reportedly freeze accounts of bitcoin users
Australian banks reportedly freeze accounts of bitcoin users
 Australian banks reportedly freeze accounts of bitcoin users
Australian banks reportedly freeze accounts of bitcoin users
 Australian banks reportedly freeze accounts of bitcoin users
Australian banks reportedly freeze accounts of bitcoin users
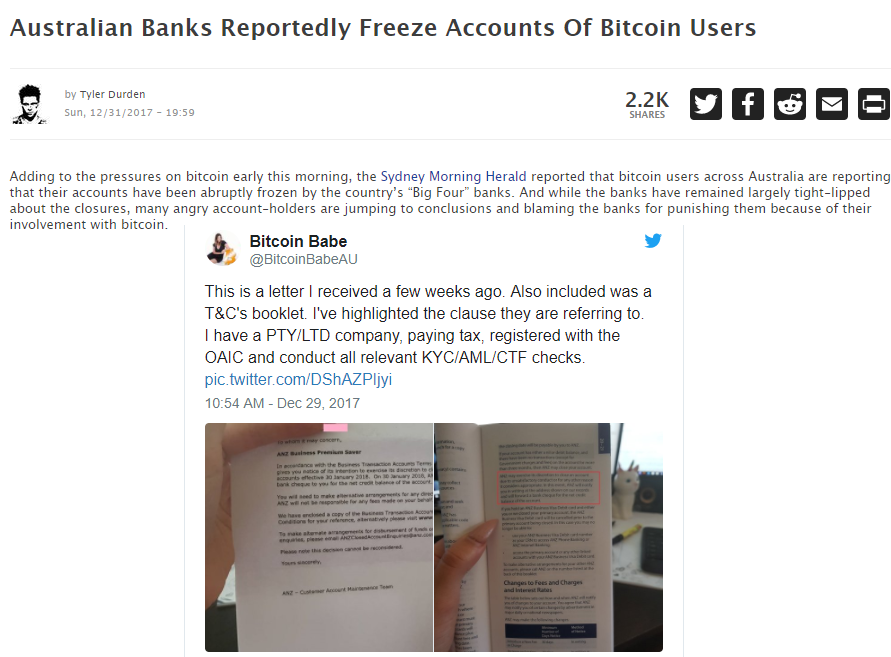 Australian banks reportedly freeze accounts of bitcoin users
Australian banks reportedly freeze accounts of bitcoin users
Related australian banks reportedly freeze accounts of bitcoin users
Copyright 2020 - All Right Reserved