
To be confirmed, transactions must be packed in a block that fits very strict cryptographic rules that will be verified by the network. These rules prevent previous blocks from being modified because doing so would invalidate all the subsequent blocks. Mining also creates the equivalent of a competitive lottery that prevents any individual from easily adding new blocks consecutively to the block chain. In this way, no group or individuals can control what is included in the block chain or replace parts of the block chain to roll back their own spends. This is just a short summary of Bitcoin.
If you want to learn more of the details, you can read the original paper that describes its design, the developer documentation , or explore the Bitcoin wiki. Make a donation. How does Bitcoin work? This is a question often surrounded by confusion, so here's a quick explanation! One excuse after the other. My total lost with these three companies was USD, I needed a major portion of this balance to pay off the down-liners who were threatening to file charges for misleading as well as fraud.
Their combined balance is approximately USD, Spread the word and help unsuspecting victims from falling prey! You could make a k weekly depending on how much you start with.
Bitcoin Mining
You are commenting using your WordPress. You are commenting using your Google account. You are commenting using your Twitter account. You are commenting using your Facebook account. Notify me of new comments via email. Notify me of new posts via email. Cryptographic Hash Functions Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol.
It should be very easy to compute an output for any given input, however it should be impossible given current knowledge of mathematics and the state of computers to compute the input for a given output even while knowing the mathematical algorithm. In this case there are many possible inputs that could add up to 10 55, , , etc. However, given the simplicity of our function one could still figure out the input relatively easily. Some cryptographic hash functions, on the other hand, are said to be unbreakable by even quantum computers. Unlike our example, each potential output should map to only one input.
If a two different inputs can produce the same output this is called a hash collision. Good cryptographic hash algorithms are resistant to such collisions. A hash function should be able to take inputs of variable size and turn them into outputs of a fixed size. Merkle Trees Now that we have the preliminaries out of the way we can start focusing in on the protocol.
The raw transaction data may look something like this: a06ea98cd40ba2ebceccaaf5eedc8e9e5a20fbdfae2d23be71aa3ad7deb3bbec4ae1aa2cf0db1df12d2afcae4ec2beb03ddef7fd06ee7ce0badc5d2ad13eade1acfbeddcf4bff2ebc19cef25abafcfbbab70ab09effffffff01b02eaadbdefaee5bfdebad7e12f7b2b1a88ac Once hashed it will look like this: 2dfa2f8aaae4a6fd93bfadf96b9c3ebffa9ad These hashes are then organized into something called a Merkle Tree or hash tree.
Bitcoin Algorithm Explained
For example a valid hash may look like this: ef1cff7aebc89da70ac0ee0 Any block whose header does not produce a hash that is less than the target value will be rejected by the network. Hash Chaining The hash of each block is included in the header of the next block as such: If an attacker wants to alter or remove a transaction that is already in the block chain, the alteration will cause the hash of the transaction to change and spark off changes all the way up the hash tree to the Merkle Root.
Six Confirmations The only exception to the above rule is if the attacker simply gets lucky.
- Recommended Programs.
- How does Bitcoin work?.
- Visions Of A Freer Future?
Share this:. Like this: Like Loading Zamri January 7, at AM. Chris Pacia January 7, at AM. Linus February 11, at AM. Thank you very much for this informative post, chris.
Chapter 5. Transactions
Chris Pacia February 11, at AM. This comment from reddit gives the probabilities. Anup August 22, at AM. Shihah Sub March 1, at PM. Johann April 27, at AM. Thank you for being so detailed. The examples are great! Venture Catalyst June 21, at AM. Katelynn Krampitz July 18, at AM. Madelyn Bartholomay November 30, at AM. Wow thank you, you article offered me great insight on how Bitcoin protocol works.
- decision bitcoin.
- Going down the rabbit hole.
- fidor bank bitcoin friendly.
Chris April 20, at PM. Marina Zemina May 31, at PM. Omar July 20, at PM. Hi — Thanks so much for your series. Rachel Gass August 19, at PM. Email: support at bitrearer dot com for further enquiries. Tommy Christ November 1, at AM. Leave a Reply Cancel reply Enter your comment here Fill in your details below or click an icon to log in:.
Decentralized Information Sharing Over Internet
Email required Address never made public. Name required. The nonce will usually be different, but it increases in a strictly linear way. Whenever Nonce overflows which it does frequently , the extraNonce portion of the generation transaction is incremented, which changes the Merkle root. Moreover, it is extremely unlikely for two people to have the same Merkle root because the first transaction in your block is a generation "sent" to one of your unique Bitcoin addresses.
Since your block is different from everyone else's blocks, you are nearly guaranteed to produce different hashes. Every hash you calculate has the same chance of winning as every other hash calculated by the network.
How Bitcoin mining really works
For example, this python code will calculate the hash of the block with the smallest hash as of June , Block The header is built from the six fields described above, concatenated together as little-endian values in hex notation:. Note that the hash, which is a bit number, has lots of leading zero bytes when stored or printed as a big-endian hexadecimal constant, but it has trailing zero bytes when stored or printed in little-endian. For example, if interpreted as a string and the lowest or start of the string address keeps lowest significant byte, it is little-endian.
The output of blockexplorer displays the hash values as big-endian numbers; notation for numbers is usual leading digits are the most significant digits read from left to right. For another example, here is a version in plain C without any optimization, threading or error checking.
Jump to: navigation , search.
 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
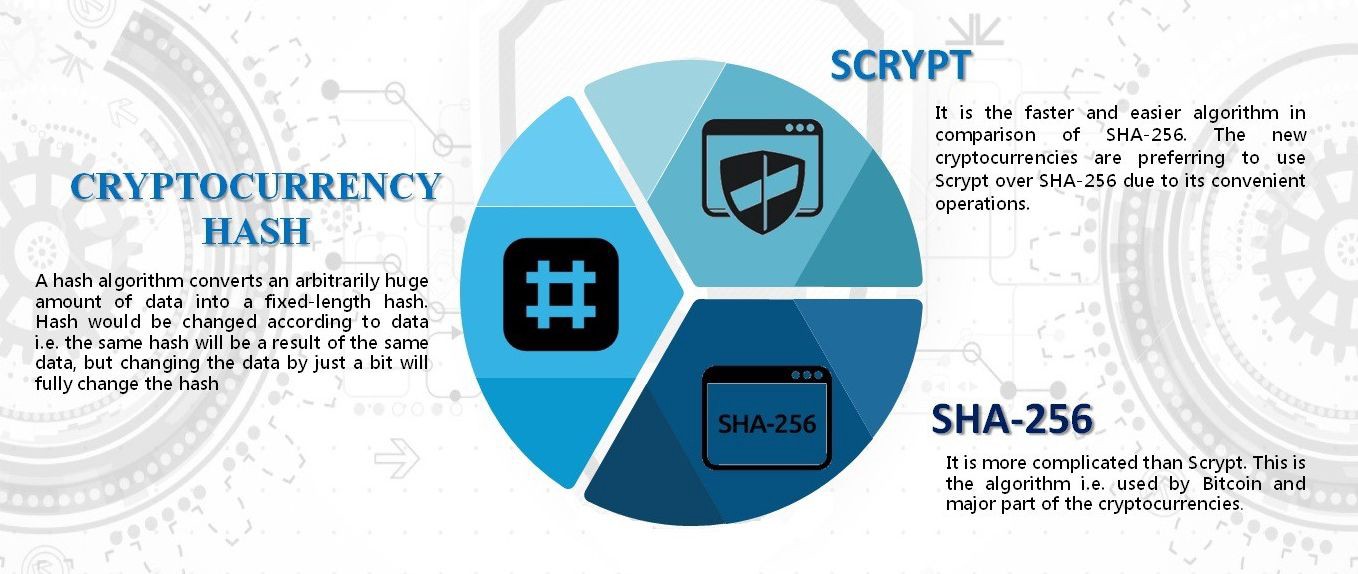 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
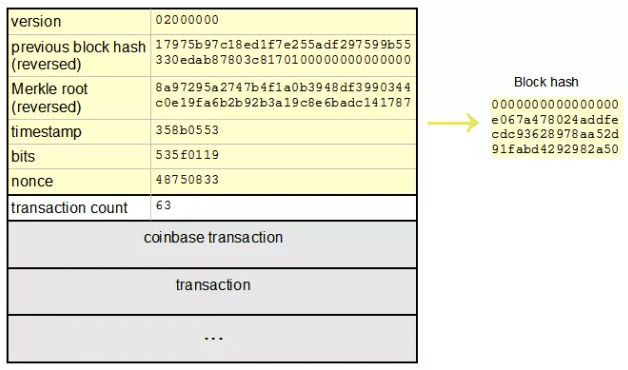 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
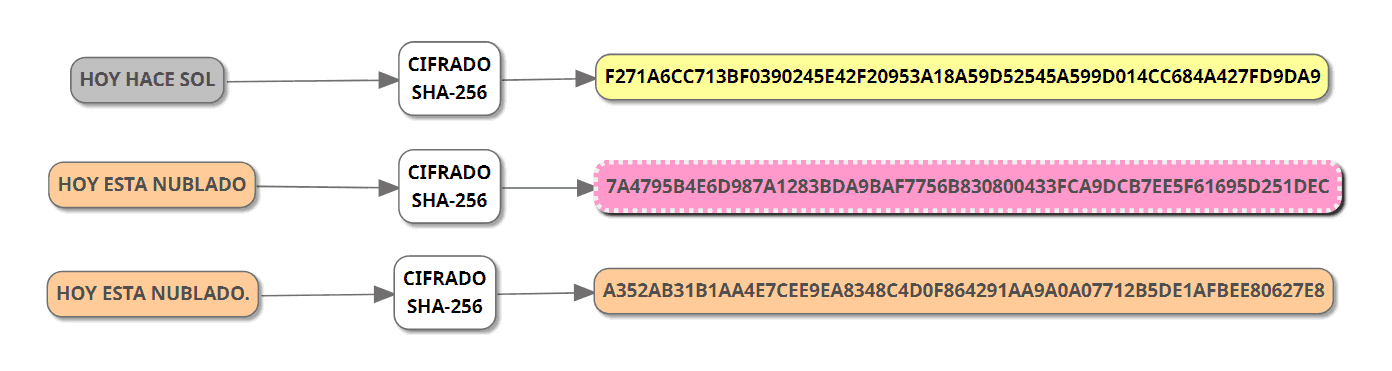 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
 What is the bitcoin algorithm used for
What is the bitcoin algorithm used for
Related what is the bitcoin algorithm used for
Copyright 2020 - All Right Reserved