Risk Assessment. Network Behavior Contacts 1 domain and 1 host. View all details.

Informative 23 Environment Awareness Reads the registry for installed applications details "iexplore. EXE" "iexplore. DLL" in "iexplore. DLL" "iexplore. All Details:. Resources Icon. Visualization Input File PortEx. Tip: Click an analysed process below to view more details. Domain Address Registrar Country upperlensmagazine. COM EMail abuse-contact publicdomainregistry. Contacted Countries.
Money thrown out the window
Download All Memory Strings 5. Quot; a conventional bibliography is a list of all the sources consulted whilst you study and write. Illustration of the simple, alphabetically arranged, selective annotated bibliography. Inquire my good friend and she advocate annotated bibliography apa. A lot of beneficial information there, plus sample annotated bibliographies in mla and apa styles. Some annotated bibliographies are meant to summarize the sources you have located.
- Powering the Brands You Love.
- Apple Daily News – 2018-10-02?
- spek laptop untuk mining bitcoin?
You need to do not need to stress about wasting hours for locating any person to write my annotated bibliography and refining your draft, simply because our professional writers and researchers will do all of the function in your case. Assuming that you keep this crucial distinction in your mind, generating an annotated bibliography is completely. Cras egestas, quam in plac erat dictum, erat mauris inte rdum est nec. AutoDetect Unicode based on Runtime Data iexplore.
Florin Petrescu
Integer eget tortor lectus. CompatibilityFlags Unicode based on Runtime Data iexplore. Count Unicode based on Runtime Data iexplore. CryptSvc Unicode based on Runtime Data iexplore. DefaultScope Unicode based on Runtime Data iexplore. This makes certain that the bibliographic type fulfills the guidelines on the publisher with minimal work. Includes roughly a hundred annotated backlinks to related web sites. That describes how bibliography objects ought to be formatted. Composing an annotated bibliography is great planning for any research undertaking. The annotation shouldn't be as well prolonged and may be properly inside of a hundred and fifty phrases.
Presentations All Presentations Product Presentation 4. Latest update. All dates. System View Description 1. IBIS models 1. BSDL files 1. Security The STM32F7x0 line comes with the proprietary code read-out-protection feature and integrates a crypto processor providing hardware acceleration for AES and encryption. Featured Videos. See All. Watch the video Recommended for you.
www.conclude.hu website review
Discover more. Part number.
Your browser is out-of-date. Don't show this message again I got it. Google Chrome Mozilla Firefox. Did you know? Receive updates. Don't show anymore. Submit E-mail address: Please enter a valid email address. A code has been sent to Not the right address? Click here to go back Enter your code: Validate Invalid code, please check the code sent to your email address and validate again.
Browse Pages
In case you did not receive any code please select 'I did not receive code'. I didn't receive code. Subscribe A code has been sent to. I want to stay informed about ST's latest news ST as data controller according to the Privacy Policy will keep a record of my navigation history and use that information as well as the personal data that I have communicated to ST for marketing purposes relevant to my interests. M Personal Coach. Just For Fun. Performance Art. Partylite Home Decor.
Public Figure.
- bitcoin aksia?
- MediaTek | Homepage.
- how to mine bitcoin mining?
- usd 32 to bitcoin?
- What is Cardano (ADA)?.
- Where to Exchange Money in Budapest – A Complete Guide ().
TV Show. Movie Character. Personal Blog. F Photographie Photographer. A Photographe Amateur Photographer. C Photo Community. C Photographie Artist. Art Artist. F photographie amatrice photographie Community.
G photographie Local Business. G photographies.
 Bitcoin adas vetel
Bitcoin adas vetel
 Bitcoin adas vetel
Bitcoin adas vetel
 Bitcoin adas vetel
Bitcoin adas vetel
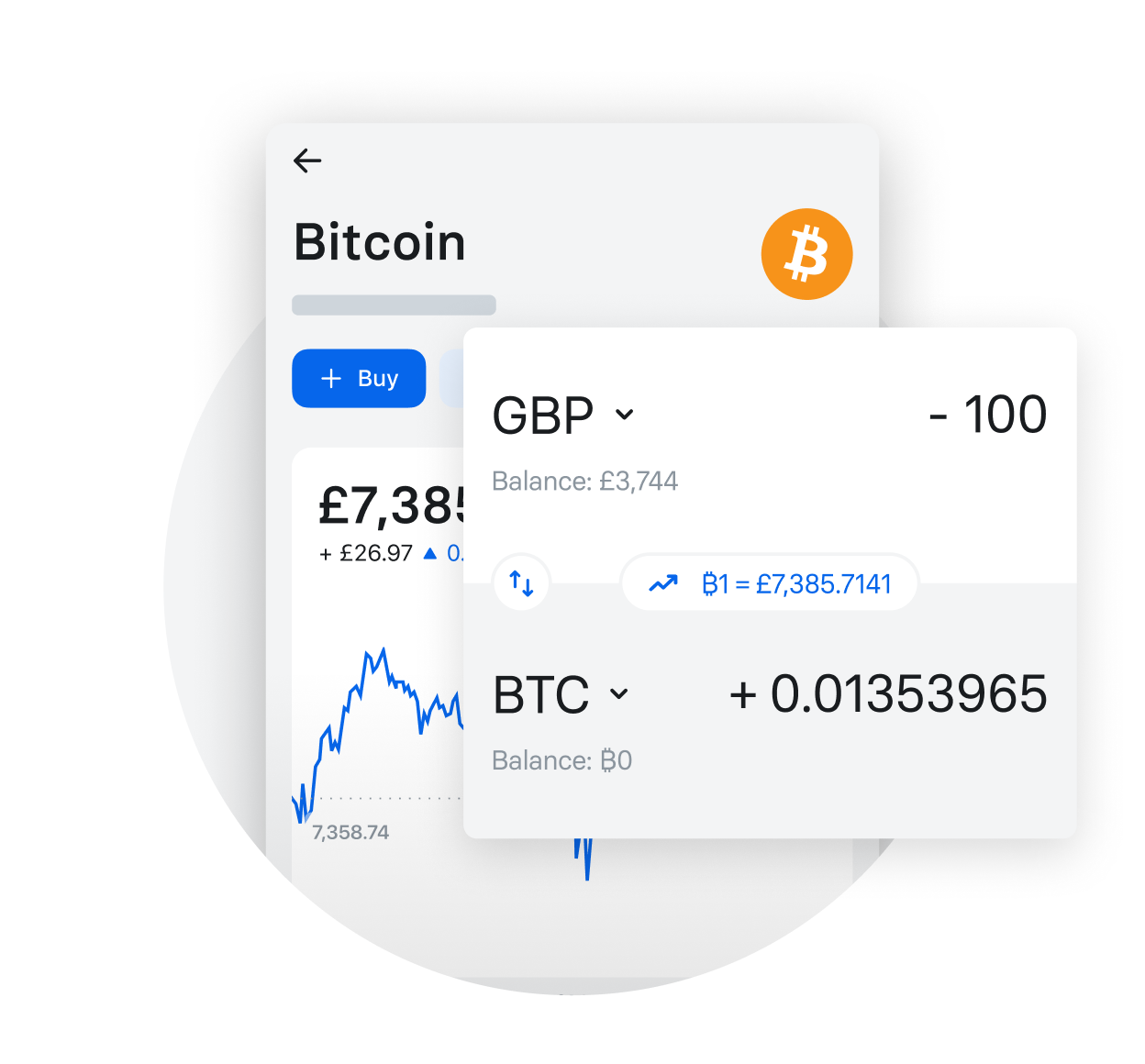 Bitcoin adas vetel
Bitcoin adas vetel
 Bitcoin adas vetel
Bitcoin adas vetel
 Bitcoin adas vetel
Bitcoin adas vetel
 Bitcoin adas vetel
Bitcoin adas vetel
 Bitcoin adas vetel
Bitcoin adas vetel
Related bitcoin adas vetel
Copyright 2020 - All Right Reserved